Can a hacker remotely view what’s on your computer screen?
In this digital era, cybercrimes are always at their peak, especially after the COVID outbreak when most IT professionals are working from home. The cybercriminals always look for the vulnerabilities in the device to attack it, and there is a better chance of finding the security loopholes and infiltrating a personal computer than the organizational computer because personal PCs are comparatively less secure. With that, the privacy concerned people always have a question in their mind – Can a hacker remotely view what they are doing on their computer screen?
Well, the answer is YES, they can. In fact, infiltrating a computer through remote access is one of the common methods used by cybercriminals.
Lately, hacking the PCs through remote access, spying, or stealing sensitive data has become common for cyberattackers. It mostly happens on the system or network that relies on the Remote Desktop Protocol (RDP).
What is RDP? How hackers exploit it to hack any system or network?
Let us find that out.
What is RDP?
RDP or Remote Desktop Protocol is a pre-installed application on Windows PC that gives remote users the ability to connect to a computer from a distance over the internet. The RDP also lets the remote users use the computer peripherals like mouse and keyboards of the connected computer and allows them to copy, cut, paste, and use other functions and applications. It is basically like using the distant device right on your system.
There are many benefits of RDP, especially in the growing “Work From Home” culture where team members can use it for accessing each other devices. Apart from it, many non-tech users can get solutions to their technical problems through remote access. They don’t have to visit the service station; almost all non-hardware-related technical issues can be solved quickly using the virtual access of their system through RDP.
Despite providing lots of functionalities and help support, the RDP makes your system vulnerable to dangerous cyberattacks. Cybercriminals can maliciously use remote access to infiltrate a system and conduct illicit activities. If it goes into the wrong hand, your computer can also become a remote-control weapon to attack more systems and networks through RDP.
But how does such a hack happen? Let us look into that.
How does the RDP is exploited?
Generally, the RDP hack happens because of the victim’s lack of awareness and loosely configured RDP on its system. If the system is connected to the internet and is listening for an RDP signal, it will respond if a remote user asks it is active. The remote user will then be provided a login screen of the victim’s desktop without letting the victim know anything about it. The attacker would be asked to enter the password for getting remote access through RDP. If the victim’s RDP is poorly configured, i.e., no strong password is enabled, then it would be easy for the intruder to get remote access to the system.
Even if the password is strong, some skillful hackers can use various techniques like traffic interception to gain the credentials and hack the system.
What can intruders do after gaining Remote Access?
After gaining remote control of the system through RDP, the infiltrators can perform many malicious tasks.
- Since the hackers are controlling your system, they can secretly install the malware programs like Trojan, Spyware, Ransomware, and others into the device.
- Through remote access, the intruders can install the backdoor into the system. Through the backdoor, they can get unrestricted access to the system any time they want and install malware, browse the internet, and use the computing power for illegal activities like crypto mining.
- The hackers can look around on the system hard disk and steal the sensitive data of the victim like private photos, banking detail, and other credentials. They can also get their hands on browsing data like history, saved passwords, and more.
- The hacker can remotely spy on you by viewing your computer screen and monitoring your activities.
How to stop RDP exploitation?
As you can see, unauthorized access through RDP can be hazardous to the system; it is essential not to let that happen. It might sound like a colossal task to restrict the exploitation of RDP; in reality, it is not that difficult. You just have to disable the remote access when not in use and limit the users.
Here is how you can do that on your Windows 10 device:
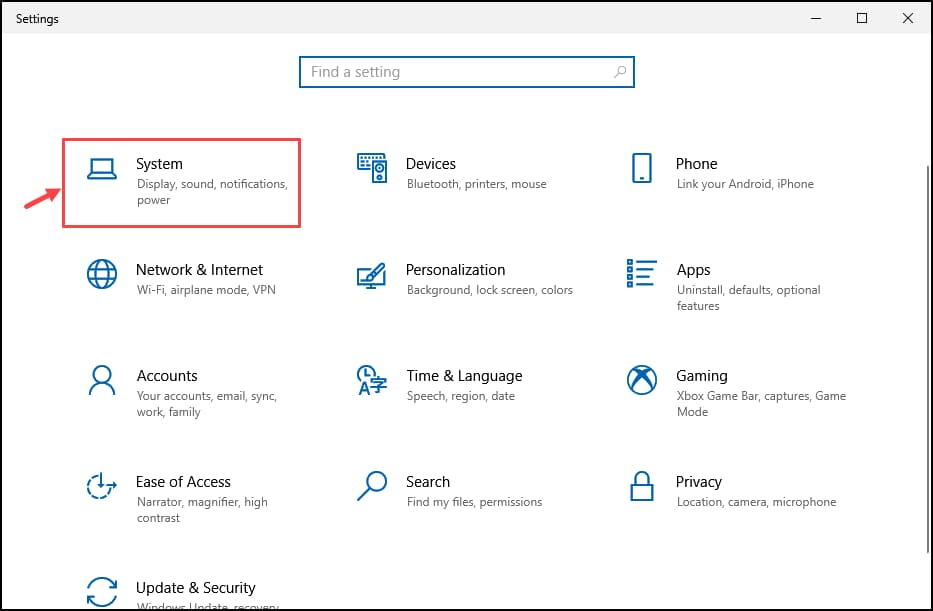
- Launch the Windows Settings and select System
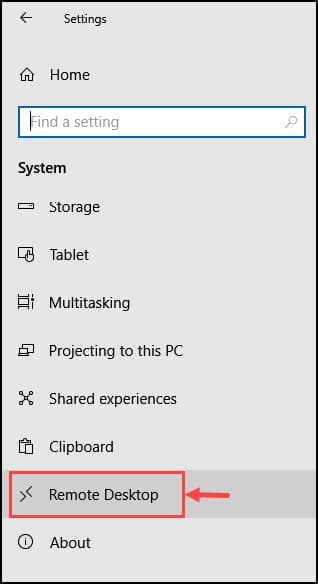
- From the left pane, select Remote Desktop.
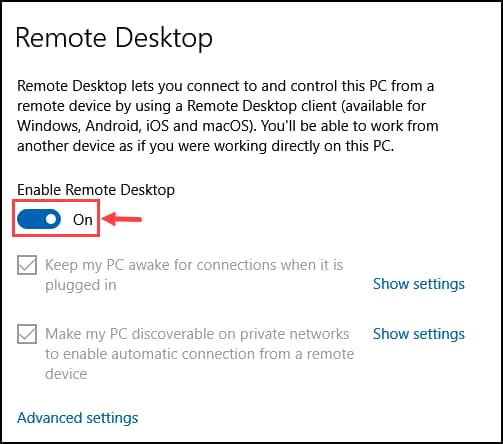
- Toggle the button to disable the Remote Desktop.
- Next, click on Advanced settings.
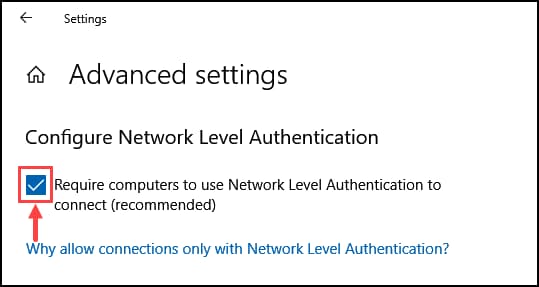
- Check the box to enable the Network Level Authentication.
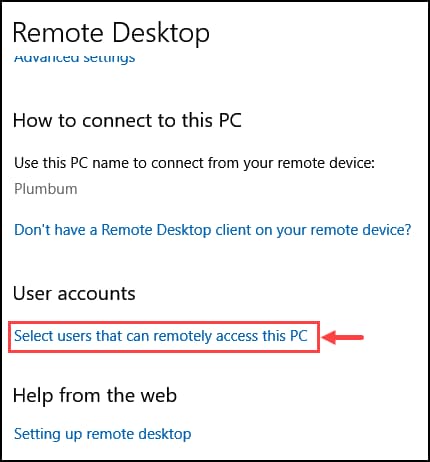
- Go back to Remote Desktop settings, scroll down, and under the User accounts heading, click on Select users that can remotely access this PC.
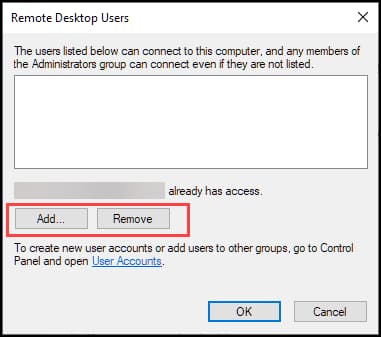
- Add or Remove the Remote Desktop Users.
Bottom Line
Remote access through RDP is an excellent way to get the virtual troubleshooting assistant for all your non-hardware Windows-related issues. However, its exploitation is more dangerous than its usability. Other than this, the infiltrators use many different techniques to gain remote access to the system. Organizations and individuals must regularly follow cybersecurity blogs and news portals to keep themselves informed of cybercriminals’ new ways to attack devices. Further, it is advised to keep Remote Access disabled until you require it. Even if you enable it, limit the users who can access the Remote Desktop so that no one unauthorized can access it.